
The challenge with vulnerability management isn’t detection, it’s determining which findings actually matter. To do this, you need to know:
Minimus’ vulnerability intelligence incorporates CISA KEV and EPSS to identify vulnerabilities most likely to be targeted, and our VEX (Vulnerability Exploitability eXchange) support makes it simple to determine if a reported vulnerability truly affects your software components. Together, these features allow users to easily identify, prioritize, and resolve vulnerabilities.
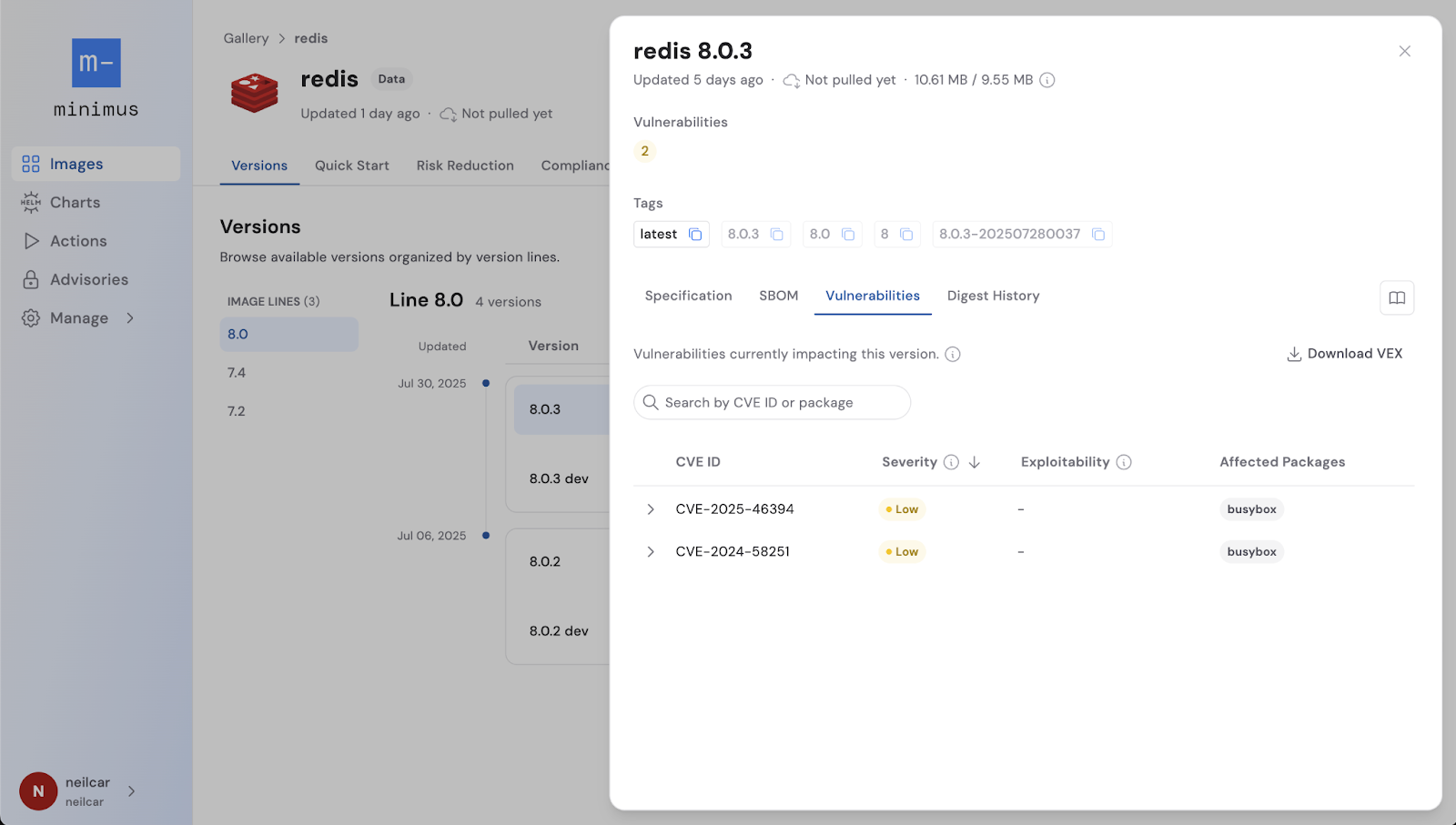
VEX enables software vendors to provide specific guidance on whether vulnerabilities affect the components they use in their software. VEX is explicitly machine-readable, enabling organizations to eliminate the manual effort. Security and development teams teams can use VEX to filter their scanning results to indicate whether a vulnerability is:
It’s quite common for a vulnerability in a particular package to not apply to software that uses that package. There are any number of reasons this may happen. For example, the vulnerability may only be exploitable in certain configurations, or the application may have other protections that make it impossible to exploit the vulnerability.
These situations create a burden for users of the software (and their vulnerability management teams). Scans show the software as vulnerable, kicking off a chain of triage, investigation, and attempted mitigation or remediation - all of which consumes developer time and distracts from real risks present in software.
Minimus supports downloading VEX information about Minimus images in OpenVEX format. VEX reports are available directly inside the Minimus console, enabling users to automatically integrate accurate vulnerability status into any workflow that consumes VEX.
While the majority of popular image scanners support Minimus’s advisories natively, exporting CVE data in VEX ensures that all approaches to scanning Minimus images are able to consume accurate information about what is (and what isn’t) impacted by specific CVEs.
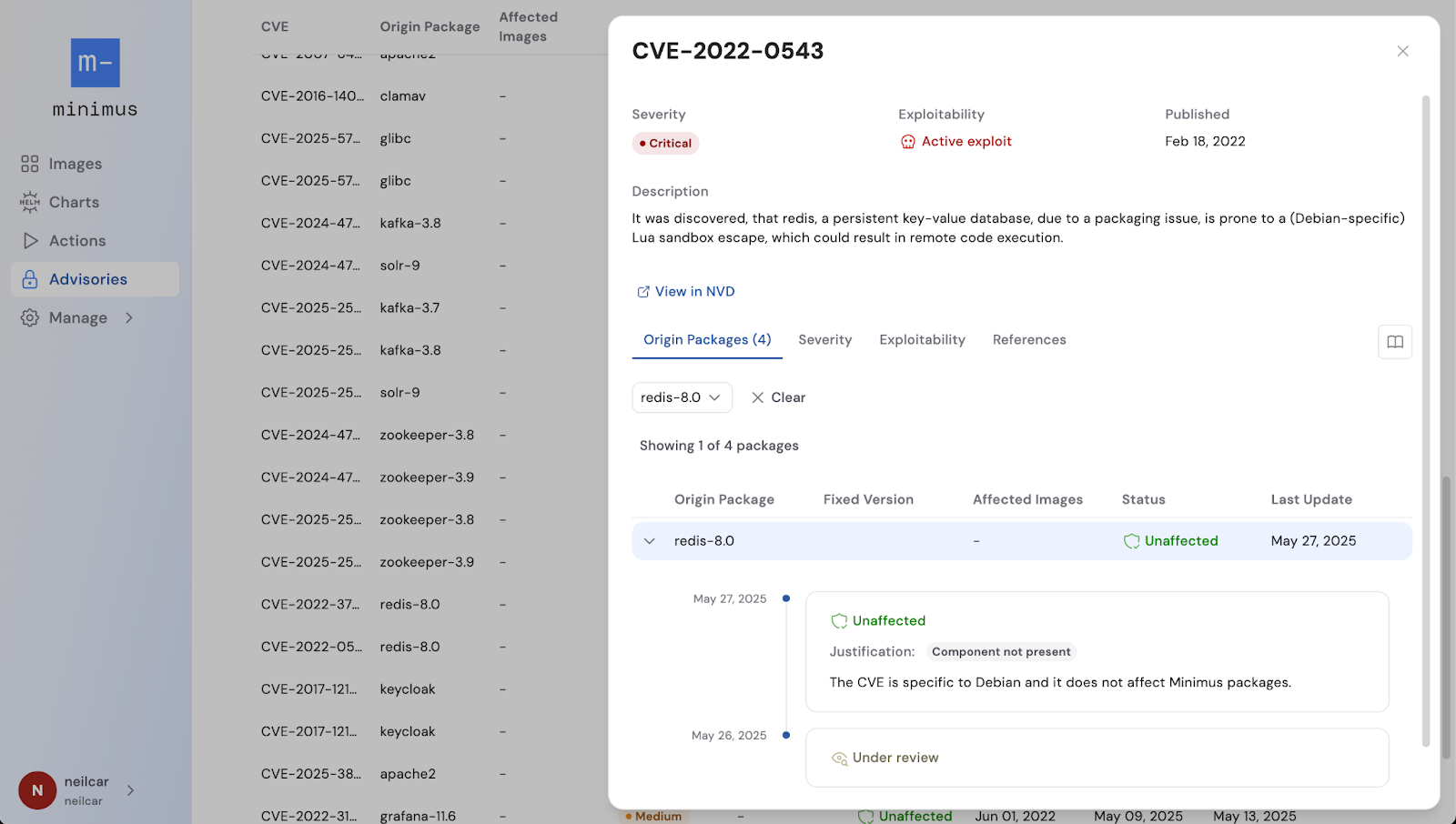
For example, if a scan detected CVE-2022-0543 in the redis package in a Minimus image, a security team might be legitimately concerned; after all, this is a critical severity CVE that is known to be actively exploited in the wild.
An analyst could manually confirm that Minimus is unaffected by searching the Advisories tab in the Minimus console, but if the organization consumes Minimus’s VEX, that step would be unnecessary. The status of the CVE would be accurately reflected in their results, and no manual work would be necessary.
VEX in Minimus gives teams a clear picture of which vulnerabilities apply and helps reduce the time and manual work required to confirm vulnerability status. When combined with other Minimus capabilities like action providers and exploit advisories, it makes triaging the small number of vulnerabilities that remain in your images straightforward and efficient. Try Minimus today to keep your focus on real risks.