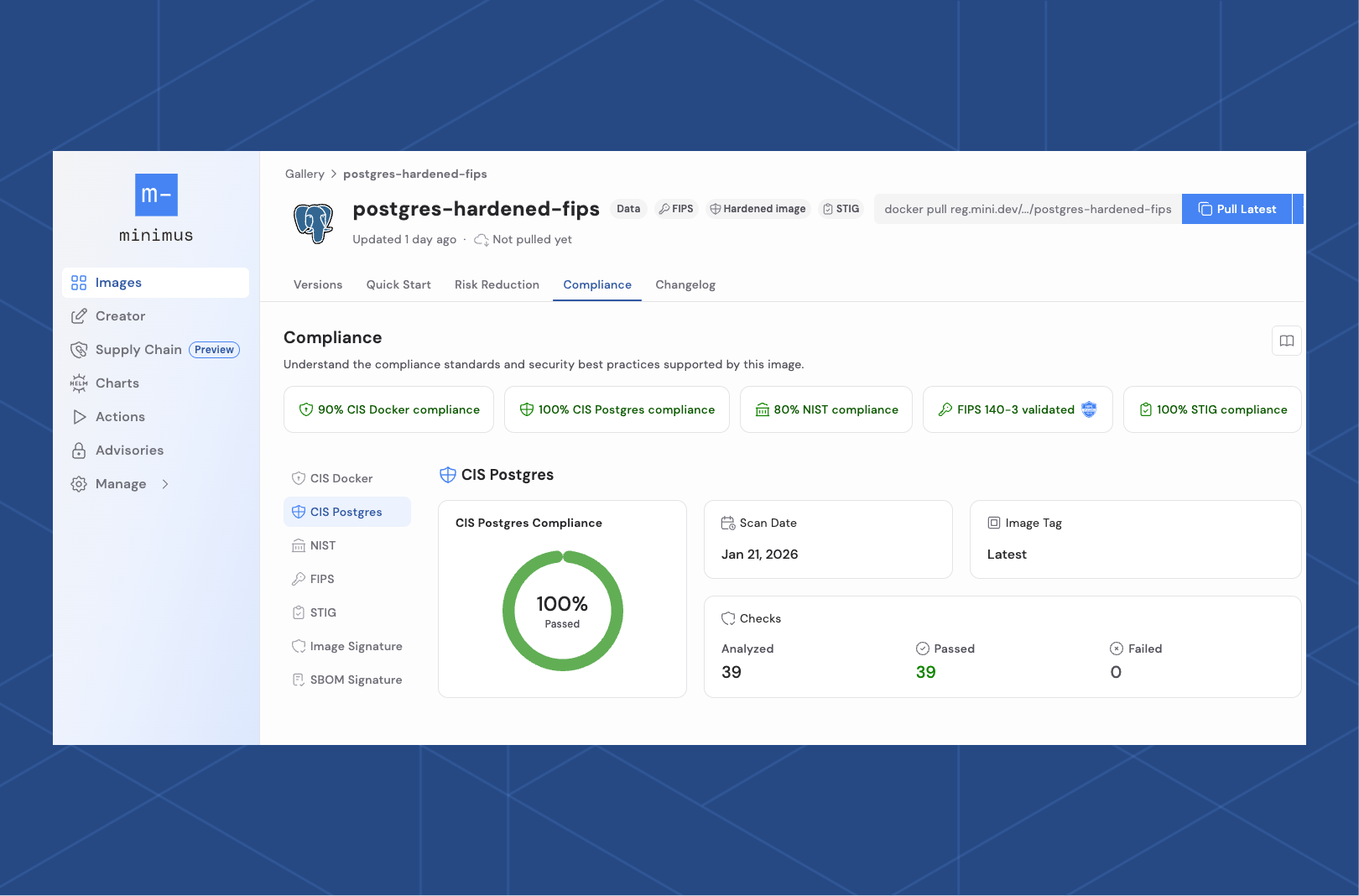
In addition to a 97%+ reduction in CVEs from their public image counterparts, all Minimus images are released as compliant by default with relevant attestation checks for CIS for Docker and NIST 800-190 checks where applicable, helping organizations achieve foundational checks as discussed prior for reaching HIPAA, NIST 800-190, FedRAMP and other related recognized industry standards.
For purpose-built application container images, there are often application specific hardening steps that still need to take place on top of the base images to not only protect and harden the application, but to further bring the application layer into compliance with the above mentioned standards.
All applications require their own unique and specific hardening procedures. That being said, these applications generally all follow related themes for hardening:
All are well documented by industry experts; application specific images delivered and maintained by respective project owners are not generally hardened out of the box or aligned to the documented best practice frameworks. This unfortunately leaves the burden and requirements on the consumer to further harden and check these after consumption of the initial images.
Recognizing an opportunity to take this a step further, we are bridging this gap by delivering application specific hardening with relevant Minimus images.
Insert our first release of relevant image hardening: the Minimus postgres-hardened image. Built on our existing postgres images (both FIPS and non FIPS) delivers a pre-hardened image for CIS Postgres out of the box, taking over the heavy lifting for organizations that require this type of hardening.
We’ve identified and applied more than 30 CIS checks, so you don’t have to manage them yourself. These controls are delivered directly in the image and can be deployed automatically into your environments.
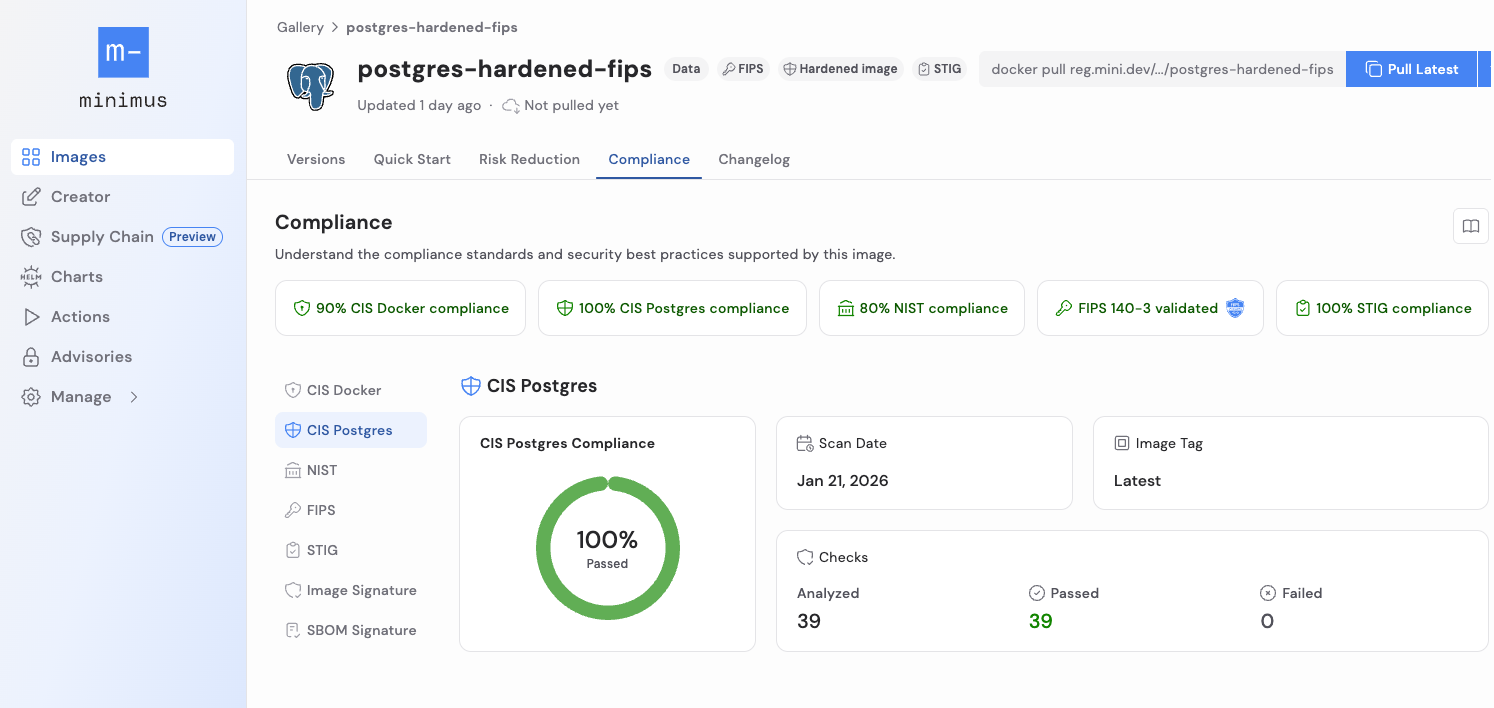
In addition to being available for consumption, you can also review dedicated dashboards for each hardened image, showing which checks have been met, making validation straightforward and enabling easy handoff of attestation evidence to auditors and other organizations.
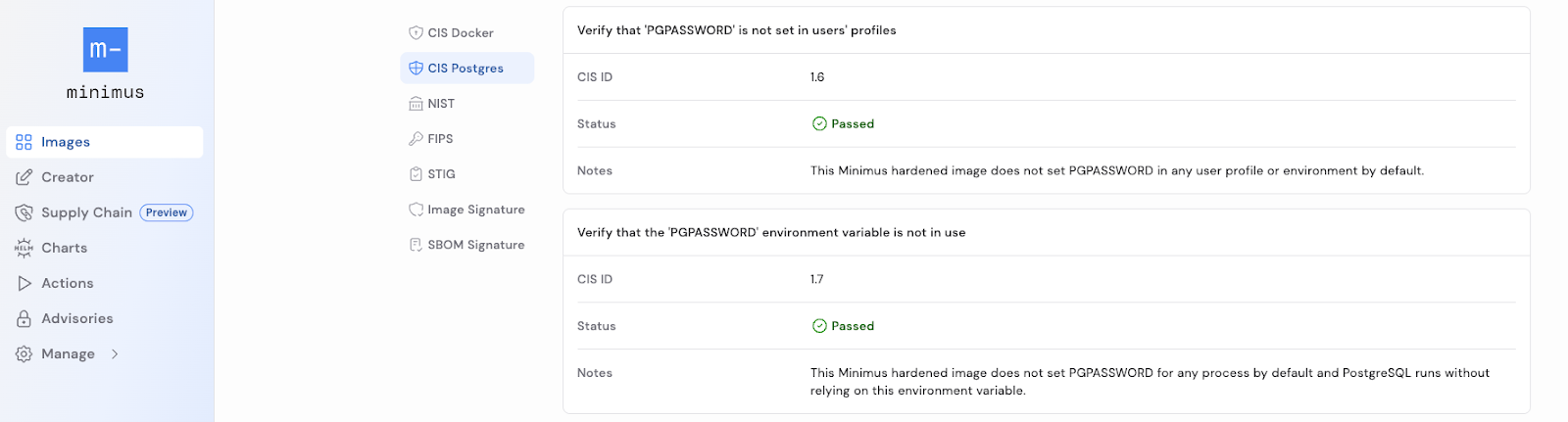
Similar to our CIS for Docker and NIST 800-190 validation dashboards, the CIS Postgres dashboard shows which checks have been validated, as well as which changes Minimus has made that deviate from the standard image. Any image that has been hardened is clearly marked with a “hardened” tag.
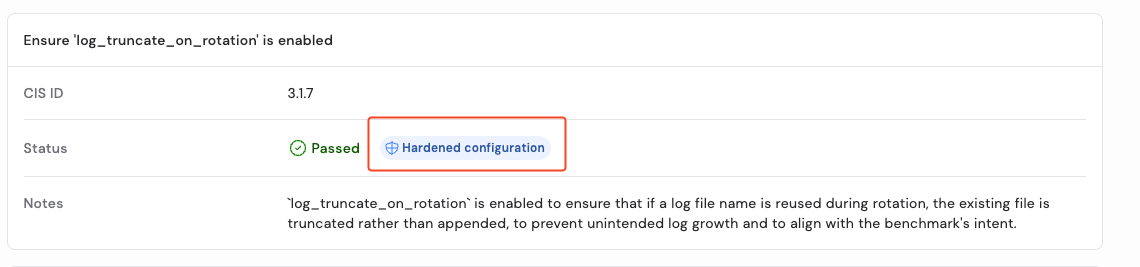
Adding an additional layer of hardening with relevant compliance mappings reduces the checking, validation, and implementation requirements that often falls on security teams, then application owners to resolve.
Whether you’re modernizing a new application or want to further reduce your attack surface, Minimus offers an additional layer to help your organization. Get a demo to see how Minimus delivers pre-hardened images and built-in validation across your environments.